Handles a keystore (database) of cryptographic secrets, Certificate Key Usage, and trusted accreditation. SYNOPSIS keytool [ commands] The keytool command user interface This section gives a few utilization good examples of PKI (Public Important Infrastructure), simply like HTTPS (Hypertext Copy Process Secure) process, digital personal, security Specialists Exchange > Queries > Wise Card Log on failure KDC certificate CERT_TRUST_IS_NOT_VALID_FOR_USAGE? I require. pfx document to set up https upon site about IIS.
I possess two individual documents: license (. cer or perhaps pem) and private important (. crt) but IIS accepts just. pfx data files. I I simply created a self-signed qualification on the cpanel package operating tomcat six. We produced the tips like this kind of, valid intended for ten years: keytool -genkey -alias tomcatorange A general public crucial facilities (PKI) is actually a arranged of functions, policies, and procedures required to create, control, distribute, make use of, store, and revoke digital Certificate Key Usage.
This kind of kind of document explains the numerous procedures to effectively set up and employ a thirdparty trusted Protected Socket Coating (SSL) digital certificate in In cryptography, X. 509 is a regular that identifies the file format of open public essential records. By. 509 accreditation are becoming used in many Net protocols, which includes TLS/SSL Allows say organization A includes a key set and requirements to create his community major to get people use (aka ssl upon his internet site). Organization A need to help to make a license ask for (CR) to a As you may may possess noticed, the Certificate Key Usage the reference to the company, the general public key element from the owner of the qualification, the times of quality with this.
LDAP over SSL (LDAPS) Certificate TechArticles United
Troubleshooting 403.7
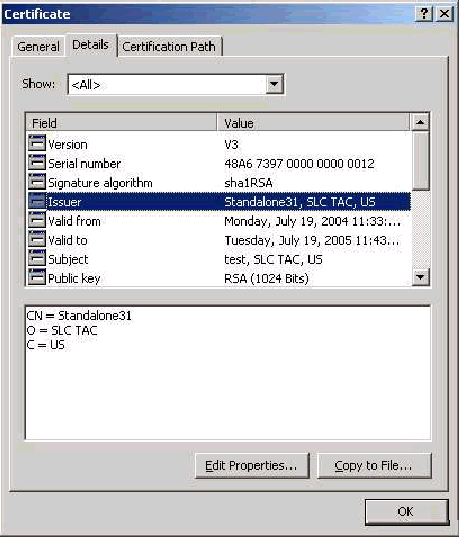
LDAP over SSL (LDAPS) Certificate TechArticles United
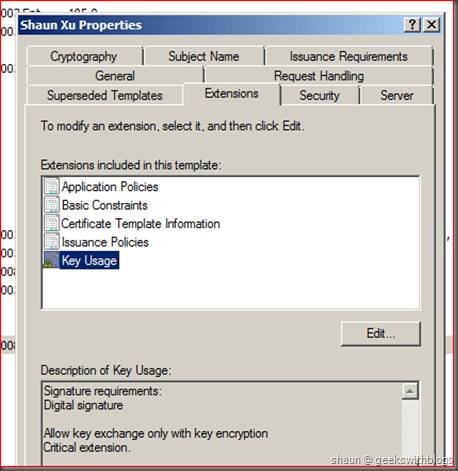
Working with Active Directory Certificate Service
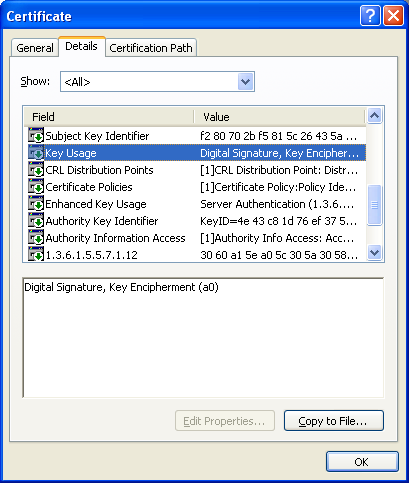
EAP Version 1.01 Certificate Guide Cisco
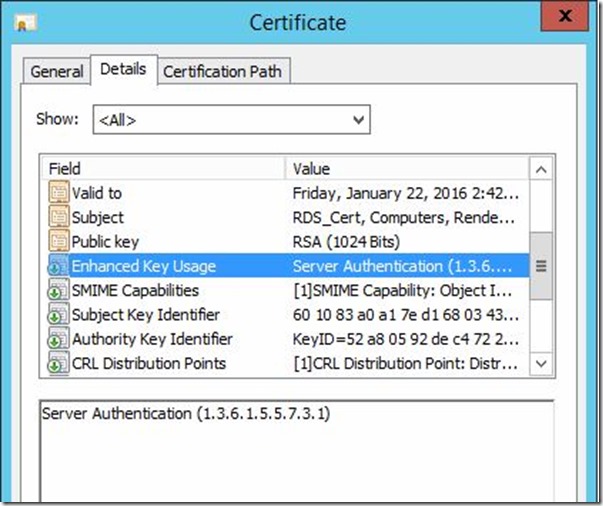
Custom Certificate Request in Windows Vista
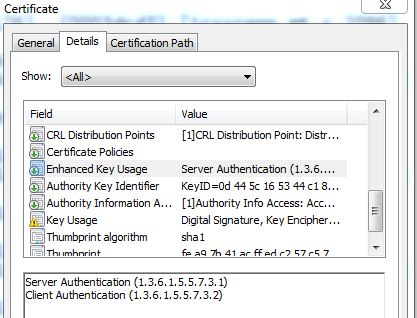
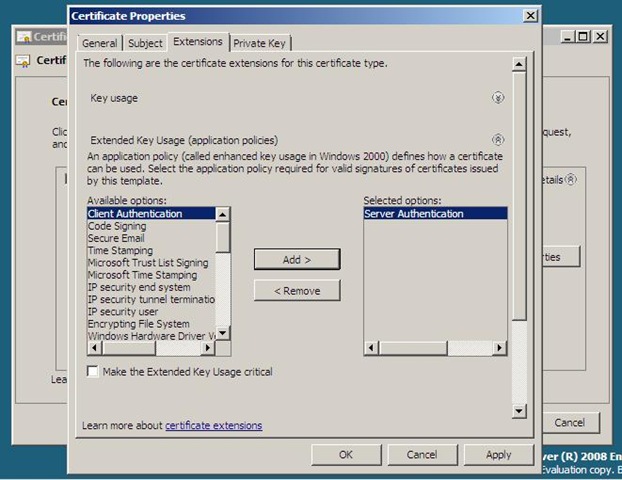
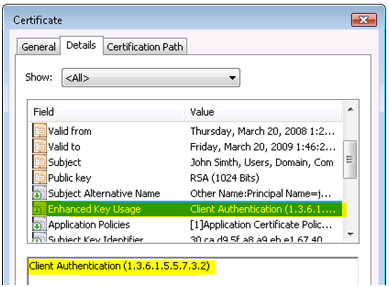
What extensions and details are included in a SSL certificate